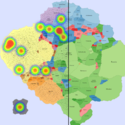
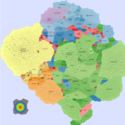
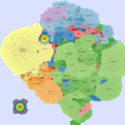
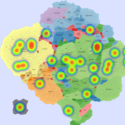
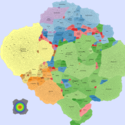
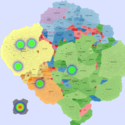
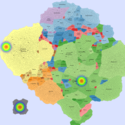
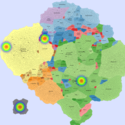
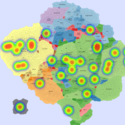
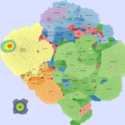
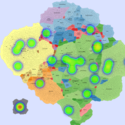
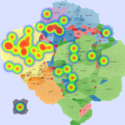
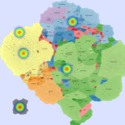
Basic Maps
We generate the following maps using the GMap framework [6], which produces geographical-like maps for a given graph. Using CAIDA data, we create an input graph where highly connected ASes are placed in closer positions. However, ASes belonging to the same country are moved from their initial positions into close proximity to avoid map
fragmentation [7].
Scenarios
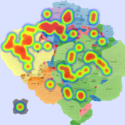
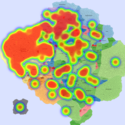
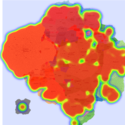
Two scenarios were created to demonstrate the usefulness of IMap. First, we use a sequence of heat maps to show the evolution of a DDoS attack. In the second scenario, we used real data [1] from a worm propagation event to study the origins of the worm and its propagation patterns. We used the CAIDA UCSD IPv4 Routed /24 Topology Dataset[2] to build the underlying AS topology in the IMap generation process.
DDos
We generated synthetic DDoS attacks of varying intensity against a monitored network over a period of 25 minutes, using several attack topologies. Background traffic was generated by the D-ITG traffic generator[3] (100 random source IP nodes) and the DDoS attack (volumetric attack) was generated by the bonesi[4] package. The data rates from the DDoS hosts were greater than those generated by background traffic sources (in terms of the number of packets, volume, and number of IP flows). Composite metric C1 combines anomaly scores related to packet count and number of IP flows. Composite metric C2 combines anomaly scores related to traffic volume and number of IP flows (more details in GlobeCom 2014).
Propagation of Code-Red Worm
In July 19th, 2001, a variant of the Code-Red worm appeared and spread very rapidly around the world. The CAIDA Code-Red Worms dataset [1] contains packet headers collected from three different network monitors. In the animations provided by CAIDA [5], the worm spread is presented by heat maps overlaid on top of geographical maps. Their conclusion was that\physical and geographical boundaries are meaningless in the face of a virulent attack". We used one of the datasets containing the data relative to the nodes (IP addresses and their respective Autonomous System) that were observed to be transmitting the worm.